Aruba Edge Services
Security for the Edge
Network security challenges have evolved significantly over the years as users have become increasingly decentralized and attacks have become more sophisticated and persistent. Traditional security approaches that focused primarily on the perimeter of the network have become ineffective as standalone security strategies. Modern network security must accommodate an ever-changing, diverse set of users and devices, as well as much more prevalent threats targeting previously “trusted” parts of the network infrastructure. Zero Trust has emerged as an effective model to better address the changing security requirements for the modern enterprise by assuming that all users, devices, servers, and network segments are inherently insecure and potentially hostile. Aruba ESP with Zero Trust Security improves the overall network security posture by applying a more rigorous set of security best practices and controls to previously trusted network resources.
ARUBA ESP: CORE ZERO TRUST PRINCIPLES
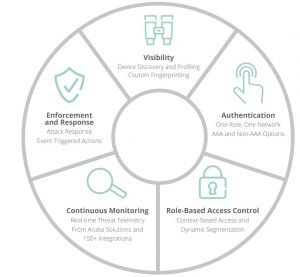
Zero Trust varies significantly depending on which domain of security is being considered. Although application-level controls have been a focal point within Zero Trust, a comprehensive strategy must also encompass network security and the growing number of connected devices, including the work from home environment. Aruba ESP with Zero Trust Security incorporates comprehensive visibility, least access micro segmentation and control, as well as continuous monitoring and enforcement. Even traditional VPN solutions are enhanced by ensuring that the same controls applied to campus or branch networks, also extend to the home or remote worker. In the age of IoT, basic principles of good network security are often difficult to implement. When possible, all devices and users should be identified and properly authenticated before granting them network access. In addition to authentication, users and devices should be given the least amount of access necessary to perform their business-critical activities once they’re on the network. This means authorizing which network resources and applications any given user or device can access. Finally, all communications between end users and applications should be encrypted.
ARUBA ESP: ADOPTING “LEAST ACCESS” AND MICRO SEGMENTATION
Once visibility is in place, applying Zero Trust best practices related to “Least Access” and micro segmentation are critical next steps. This means using the best authentication method possible for each endpoint on the network (i.e. full 802.1X and multi-factor authentication for user devices) and applying an access control policy that only authorizes access to resources that are absolutely necessary for that device or user. Aruba ClearPass Policy Manager enables the creation of role-based access policies that enable IT and security teams to operationalize these best practices using a single role and associated access privileges that are applied anywhere on the network – wired or wireless infrastructure, in branch or on campus. Once profiled, devices are automatically assigned the proper access control policy and segmented from other devices via Aruba’s Dynamic Segmentation capabilities. Enforcement is provided by Aruba’s Policy Enforcement Firewall (PEF), a full application firewall that is embedded in Aruba network infrastructure. Aruba infrastructure also utilizes the most secure encryption protocols such as the WPA3 standard over wireless network connections.
ClearPass Policy Manager also integrates with a wide variety of authentication solutions enabling the use of multi-factor authentication and the ability to force re-authentication at key points throughout the network. Through the ClearPass ecosystem, customers can also easily incorporate other solutions to meet Zero Trust requirements related to contextual information and other security telemetry. This means ClearPass can integrate with a wide variety of solutions such as Endpoint Security tools to make more intelligent access control decisions based on a device’s posture. Access control policies can also be changed based on which type of device is being used, where the user is connecting from, and other context-based criteria.
CONTINUOUS MONITORING AND ENFORCEMENT
With role-based access control in place to enforce granular segmentation, ongoing monitoring of users and devices on the network make up another Zero Trust best practice. This addresses risks related to insider threats, advanced malware, or persistent threats that have circumvented traditional perimeter defenses.
Engage with our presales specialists by contacting us on sales @ eworld.com.mt for more details
